THE TOTAL HIPAA
Resource Library

Mastering HIPAA Compliance with Email Encryption
The Health Insurance Portability and Accountability Act (HIPAA) mandates that covered entities safeguard Protected ...

3 Reasons Insurance Agents Need to Follow HIPAA
Health insurance agents became covered under HIPAA with the HITECH Act of 2009.
The inclusion of insurance ...

Working Remotely While Staying HIPAA Compliant: Using a Virtual Private Network (VPN) vs. SSL/TLS in a HIPAA Environment
Whether you’re working from home, your local coffee shop, or from the airport between layovers, you will likely ...

How to Use HIPAA to Defend Against Common Cybersecurity Attacks
While much of the anti-malware technology we have to protect us from hackers has become increasingly more ...

Microsoft Announces End of Support for Internet Explorer
Internet Explorer was once one of the biggest players in the browser game, but now it’s coming to its end of days. ...

HIPAA Risk Assessment for Insurance Agents: What to Expect
As an insurance agent, you may be wondering how the Health Insurance Portability and Accountability Act (HIPAA) ...
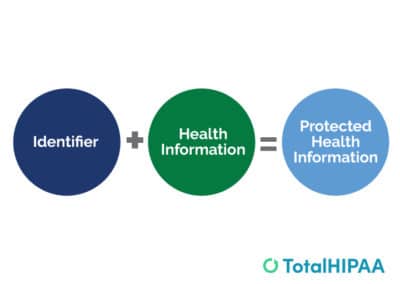
Protected Health Information (PHI): Everything You Need to Know about HIPAA and PHI
Curious about PHI? Dive into our featured blog post to uncover the answer to the question: "What does PHI stand ...

HIPAA Audits for Insurance Agents
Insurance agents who handle protected health information (PHI) are required to comply with the Health Insurance ...

What is NIST 800-50 and How Should It Inform Your HIPAA Training?
For organizations that deal with sensitive client or employee information, (e.g., Medical Practices, Employer ...

How HIPAA Safeguards Can Help You Safely Transmit PHI
For organizations handling Protected Health Information (PHI), cybersecurity attacks and other security threats ...

New OCR Guidelines for Defending Against Cybersecurity Attacks
In a recent statement, President Biden encouraged private sector companies to give increased attention to their ...

HIPAA Compliance in Marketing and Communications for Insurance Agents
Are you an insurance agent who handles protected health information (PHI)? If so, you must comply with the Health ...

Password Best Practices Are Changing. How Should You Adapt?
As technology becomes more and more sophisticated, so do the strategies hackers use in data breaches. Now more ...

HIPAA and ERISA: Everything You Need to Know
Understand the key role of ERISA and HIPAA, rules that oversee employee benefits and protect health data. This ...

Deadline for Reporting Small HIPAA Breaches Is March 1st
HIPAA breaches involving fewer than 500 individuals which occurred during 2021 must be reported to the ...

Top 10 Total HIPAA Blogs of 2021
Throughout 2021, Total HIPAA has focused on providing information that will keep your organization HIPAA compliant ...

The Ohio Data Protection Act and HIPAA Compliance
Every day, there seems to be a new headline about another organization whose data security has been breached. It’s ...

What You Need to Do to Be HIPAA Compliant After Signing a BAA
Before agreeing to trust another business with your data, there are several precautions you need to take. Firstly, ...

How to Ensure HIPAA Compliance While Storing PHI on the Cloud
For healthcare companies, cloud data storage is a popular and practical alternative. The worldwide Healthcare ...

Your Cybersecurity Questions Answered!
Thanks to everyone who attended our November 4th webinar, Don’t Become the Next Cybersecurity Scary Story! We are ...
No results found.
Take control of your compliance.

