


HIPAA Compliant Cloud Backup Services
This week, we’re defining cloud backup and explaining why it’s important, then we’ll take a look at several cloud backup HIPAA compliant vendors that specialize in small to medium-sized business solutions. The cloud vendors we chose to review are all willing to sign a...Are Your Clients HIPAA Compliant?
This article and infographic was originally published by the Maurice A. Deane School of Law at Hofstra University’s Online Master’s in Health Law and Policy program.1 The Gravity of HIPAA HIPAA compliance is aimed at maximizing privacy and data security when it comes...
Employer Group Breach Woes
There are HIPAA Responsibilities for Businesses This week, two incidents of employer group breaches involving unauthorized access to employees’ Protected Health Information (PHI) have come to light. The first incident involves a hacking/IT event targeting the...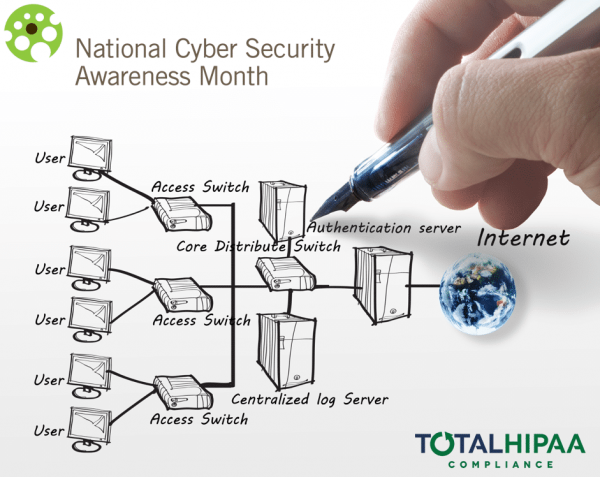
Are You Participating In National Cyber Security Awareness Month?
October is designated National Cyber Security Awareness Month (NCSAM), an effort that the U.S. Department of Homeland Security and the National Cyber Security Alliance, as well as others partners, to highlight the importance of smart cybersecurity. Massive breaches...
Penetration Testing: Adding Value to Your Security Posture
As you strive to make HIPAA compliance one of the most important aspects of your organization, you likely have technology and procedures in place to protect yourself from data theft. 2017 has seen tons of ransomware attacks, and you don’t want to be a victim, too. You...
A Look Into an HHS OCR Desk Audit
Since 2016, the Office for Civil Rights (OCR) in the Department of Health and Human Services (HHS) has been conducting Phase 2 of the HIPAA Audit Program. Through the use of desk audits, HHS has randomly requested documentation and evidence from organizations required...
Preparing For Every Disaster
While recovery from Hurricane Harvey is under way and evacuations begin in Florida as Irma approaches, Total HIPAA wants to remind you of the importance of a Disaster Recovery Plan. Fires in the west, flooding from Harvey and destruction expected from Irma are exactly...
Smishing – The Next Cyber Threat
It seems like cyber attackers and scammers have been making headlines more and more lately as they’re finding different ways to kidnap your data and hold it hostage. It’s no surprise that another type of attack is rearing its ugly head more frequently. Smishing. Heard...
