
What to Do If a Client or Auditor Asks for a Pen Test
If your organization handles sensitive information, you may encounter a client, security auditor, or third party asking for a copy of your most recent penetration test. This ...

Is Gmail’s Confidential Mode HIPAA Compliant?
Gmail is exceedingly popular among email users for both personal and business purposes — and for good reason. It’s the second most widely-used email platform, after Apple ...

Basic HIPAA Guidelines: Annual Update 2022
We recently hosted a webinar, “Annual HIPAA Requirements and Security Standards,” in which we discussed annual HIPAA requirements, document review, and the compliance ...

Working Remotely While Staying HIPAA Compliant: Using a Virtual Private Network (VPN) vs. SSL/TLS in a HIPAA Environment
Whether you’re working from home, your local coffee shop, or from the airport between layovers, you will likely need to connect to your organization’s network. A public or ...

How to Use HIPAA to Defend Against Common Cybersecurity Attacks
While much of the anti-malware technology we have to protect us from hackers has become increasingly more sophisticated, so have attackers’ methods. According to the U.S. ...

Microsoft Announces End of Support for Internet Explorer
Internet Explorer was once one of the biggest players in the browser game, but now it’s coming to its end of days. Starting June 15, 2022, Microsoft will end support of ...

HIPAA Risk Assessment for Insurance Agents: What to Expect
As an insurance agent, you may be wondering how the Health Insurance Portability and Accountability Act (HIPAA) impacts your business. The law aims to protect patient ...
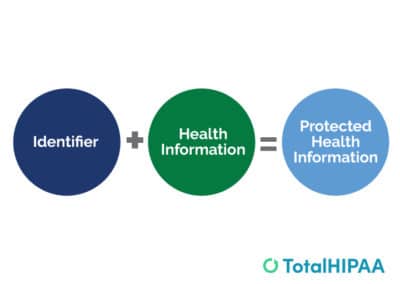
Protected Health Information (PHI): Everything You Need to Know about HIPAA and PHI
Curious about PHI? Dive into our featured blog post to uncover the answer to the question: "What does PHI stand for?" Gain valuable insights into the significance of ...

HIPAA Audits for Insurance Agents
Insurance agents who handle protected health information (PHI) are required to comply with the Health Insurance Portability and Accountability Act (HIPAA). One way to ensure ...

HIPAA Training for Insurance Agents: Requirements and Strategies
Insurance agents who handle protected health information (PHI) are required to comply with the Health Insurance Portability and Accountability Act (HIPAA). One important ...
No results found.
Featured Resources

Is Gmail HIPAA Compliant?
Gmail is not automatically HIPAA compliant, however, you can implement security measures…
Read More →

Free Download: HIPAA 101
How well do you meet basic HIPAA regulations? Our HIPAA Compliance 101 resource outlines the key…
Download Now →

How to Use HIPAA to Defend Against Common Cybersecurity Attacks
While much of the anti-malware technology we have to protect us from hackers has become…
Read More →
Free Webinar: Annual HIPAA Requirements & Security Standards
In this webinar, we discussed annual HIPAA requirements, document review, and the compliance…
Watch Now →
Join Thousands of
Satisfied Organizations
Streamline your compliance with Total HIPAA and reclaim valuable time for your core business.

