

The 2025 Workday & Salesforce Breach: A HIPAA Wake-Up Call for Vendor Management
More Than Just Another Tech Headline The widespread 2025 data breach affecting users of Workday and Salesforce is far more than a distant technology problem; it is a critical and urgent case study for every healthcare provider, employer group health plan, health...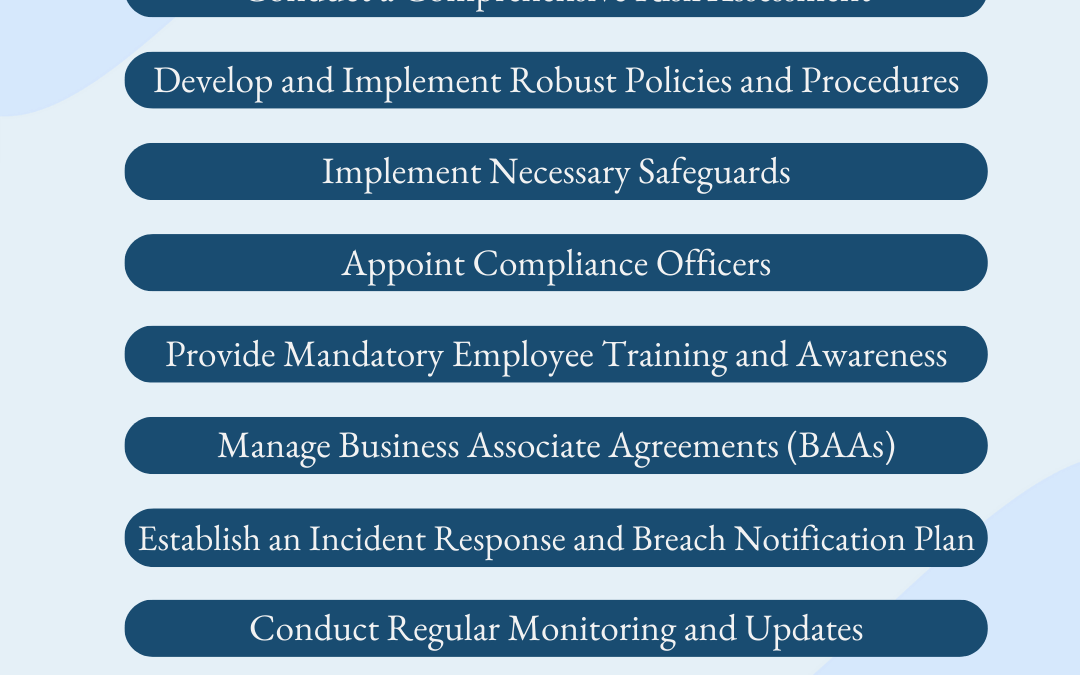
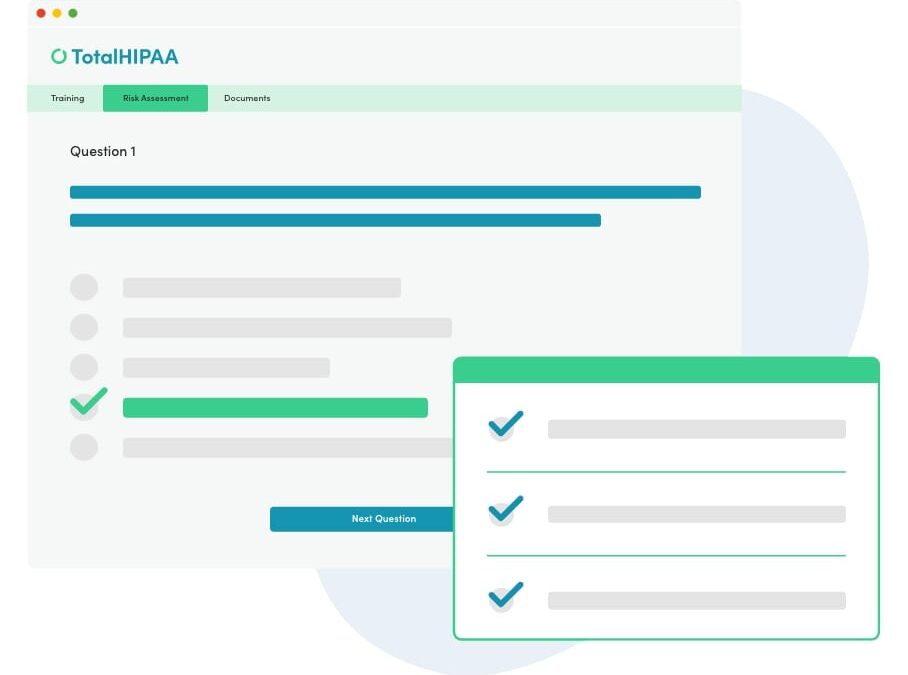
The Ultimate Guide to Making a Company HIPAA Compliant
In today’s interconnected world, safeguarding sensitive information is paramount, especially in healthcare. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law designed to protect an individual’s Protected Health Information...Essential Guide to Email Authentication and Deliverability: How to Configure DMARC, SPF, and DKIM Records
How to Configure DMARC, SPF, and DKIM Records *This process is technical and requires access to your Domain Name Server (DNS). It’s recommended to have an IT professional handle these configurations to avoid potential issues. If you proceed yourself, first, back...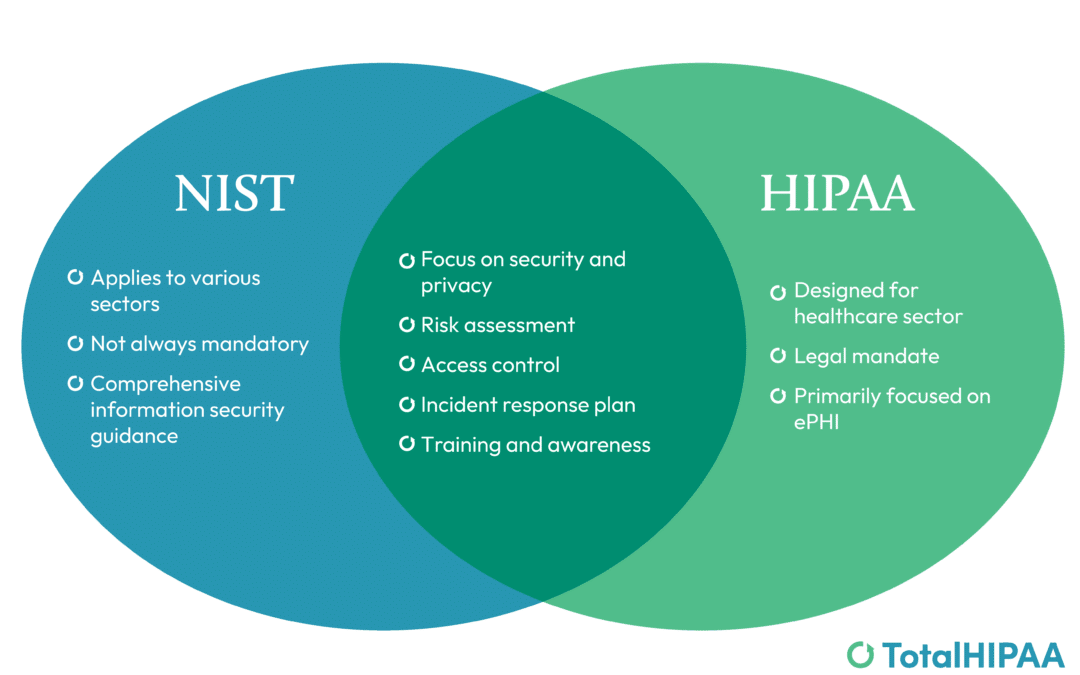
Comparing HIPAA and NIST
In the ever-evolving landscape of data security and privacy, two key frameworks have emerged as significant players: HIPAA and NIST. Both emphasize the importance of safeguarding sensitive information, but they have key differences in their scope, mandate, and...
